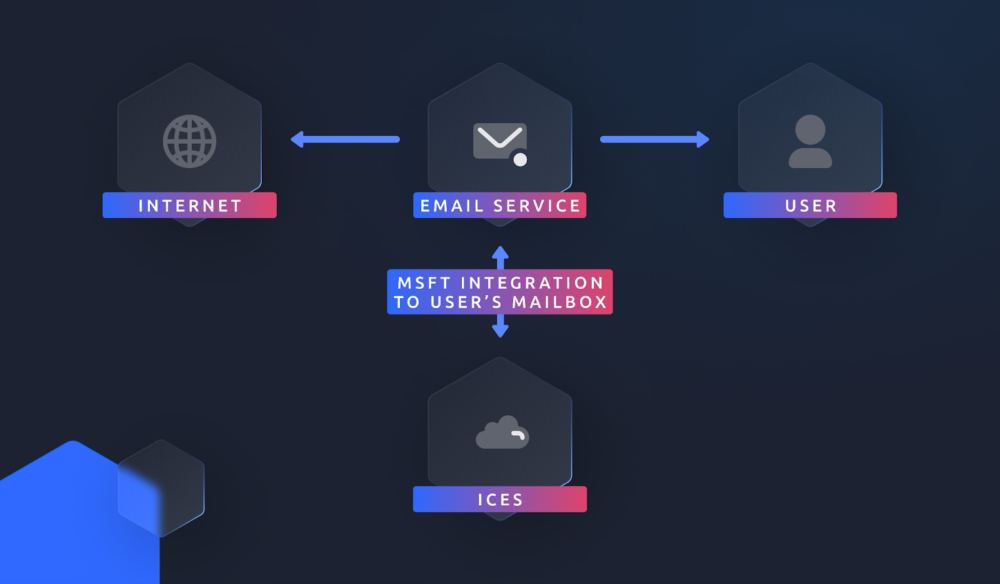
Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises.
We are excited to announce the release of our M365 Add-In, simplifying the deployment of the Tessian Cloud Email Security Platform. Tessian’s M365 Add-In (Office Add-In) comes together with the M365 API (Microsoft Graph API) to offer the M365 Integration an industry-first click-through deployment with Microsoft 365 providing email threat defense and insider risk protection in minutes, without the need to deploy or maintain client-side code or a gateway.
The decline of gateway security solutions
The effectiveness of legacy approaches to email security has been in the crosshairs for quite some time, primarily due to the declining effectiveness of Secure Email Gateway (SEG) and the pervasiveness of threats hitting inboxes, with email responsible for over 90% of cyber attacks.
Now Gartner predicts that by 2025, 85% of organizations will embrace cloud-first principles. This rapid acceleration to the cloud has opened up a world of possibilities for seamless integrations with cloud security providers. Most enterprises adopt cloud-hosted productivity suites such as Microsoft 365, which natively provides SEG capabilities. But it’s more than just a duplication of capabilities. The rapid shift to the cloud and the ever-changing threat landscape has exposed a once sturdy and reliant email defense to become vulnerable and ineffective in safeguarding users and data from advanced threats and insider risks.
Today security leaders are abandoning their point solution demanding SaaS solutions that integrate with their cloud solutions—removing that once overburdening, legacy solution for a more intelligent and straightforward approach.
Rise of Cloud Email Security?
The email security market was on hold for years. But then, according to the Verizon Data Breach Report, in 2022, human error was responsible for 82% of breaches. On average, phishing and business email compromise cost an organization $4.9 million annually, ten times the cost of DDOS and ransomware attacks combined. The need for a new approach to email security is no longer a choice.
These solutions have not disappointed. The Rise of Cloud API-Enabled Email Security. CAPES/ICES solutions that have capitalized on a market ready for change.
M365 Integration. Effortless for the security team.
Today Tessian has introduced an Integration that places power back into the security team’s hands—integrating in seconds with your M365 environment, leaving you protected in minutes.
However, this Integration comes with a difference. As with most ICES vendors, they are integrated via a graph API into the cloud-productivity suite, focused only on threats coming into the organization. Because of this, they are still leaving the organization exposed to insider risks and sensitive data loss. They are still operating as a point solution, unable to replace legacy email controls fully.
Tessian’s M365 Integration is different. A new and simple integration consisting of the M365 API (Graph API) and M365 Add-In (Office Add-In) allows complete email protection against a wide range of threats.
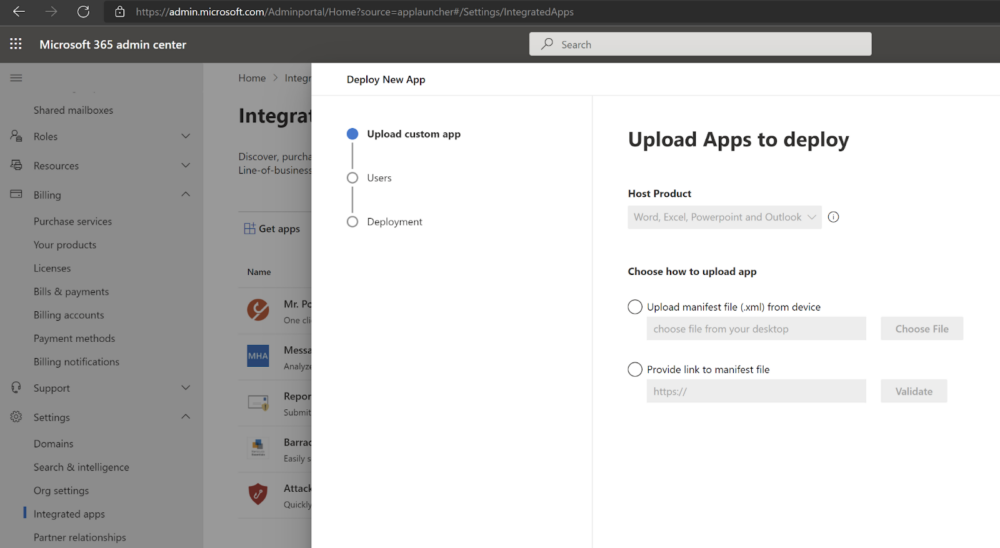
The Integration requires Mailbox API Connection and an XML manifest file to be uploaded to the M365 Admin center.
This deployment follows just a few simple steps:
- Enable connection to M365 Tenant
- Grant required permissions to enable email security
- Add directory groups to sync
- Add mailboxes by group, user, or both to protect required end-users.
- Download the M365 Add-In manifest file and upload it to the M365 Admin Center.
Once the API has synced and the manifest is deployed when a user next opens a supported Outlook client Tessian’s Cloud Email Security Platform protects them.
What is an Office Add-In
Office Add-Ins (sometimes called Web Add-Ins) allow 3rd parties to build solutions that extend to Microsoft 365 applications. These solutions can run in Microsoft 365 applications, such as Outlook, across multiple platforms, including Windows, MAC, iPad, and a browser.
Office Add-Ins are deployed centrally in the M365 Admin Center and don’t involve rolling out client-side software or routing emails through a gateway. They have low management overhead, no complex configurations, and no manual updates meaning security teams can focus on what matters most—protecting their organization.
Integration flows
The M365 Add-In (Office Add-In) requires M365 API connections to be fully functional, which is why the M365 Integration exists. As both are required to secure an organization, Tessian has built them together to make deployment as simple and easy as possible.
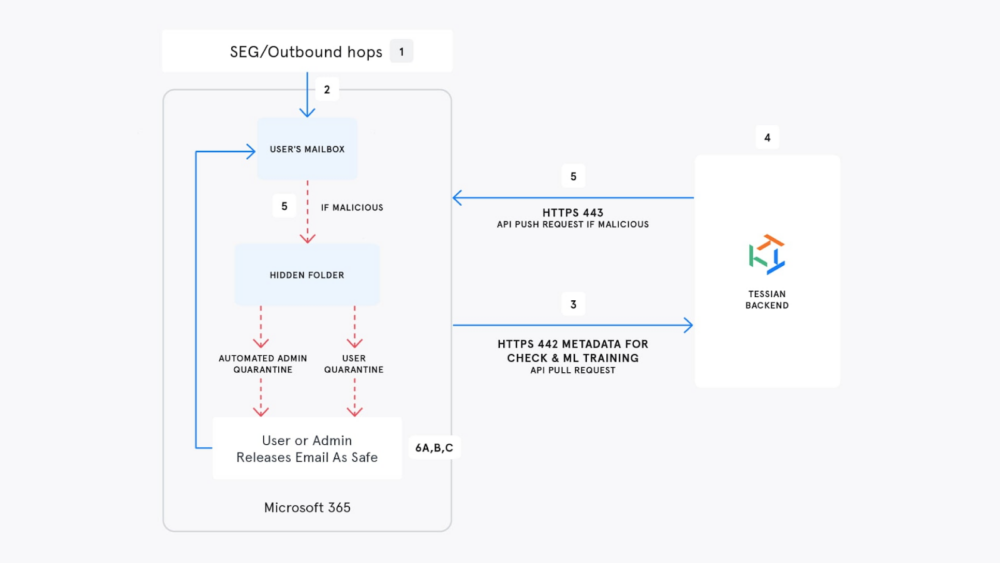
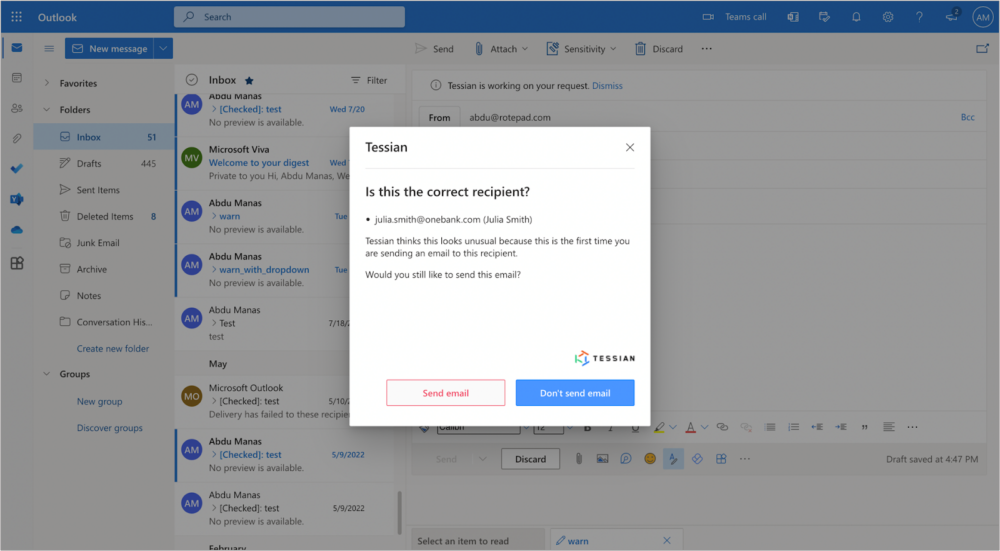
This new level of protection means that when the email check process starts, the M365 Add-In intercepts the email, checks the email with the Tessian Cloud Email Security Platforms behavioral intelligence model, and then the result is returned, either allowing the email to be sent or showing a warning message to the end-user and preventing a potential data loss incident.
Mistakes happen, and end-users should know they are protected.
When end-users receive or send an email, they know an automated check will occur to prevent an advanced phishing attack from hitting their inbox.
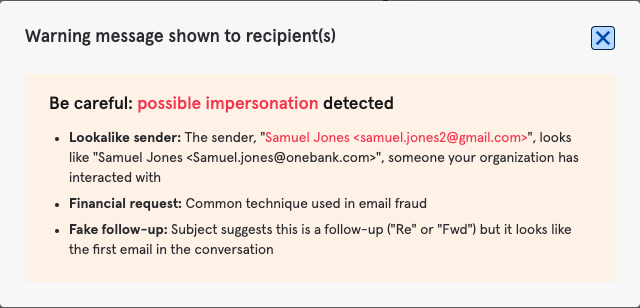
Likewise, when a mistake happens, such as autocomplete on an email address, an end-user is warned of the potential error to not only avoid the potential data breach, but they are coached in the moment.
If the email is okay, the email continues on to its desired destination.
The time is now
Tessian is built with simplicity and speed to protection in mind. And when 82% of breaches are caused by human error, the time is now to ensure you have the best email protection deployed.
Hundreds of the world’s organizations trust the Tessian Cloud Email Security Platform, which now offers a simplified deployment and better end-user experience for Microsoft 365 environments.