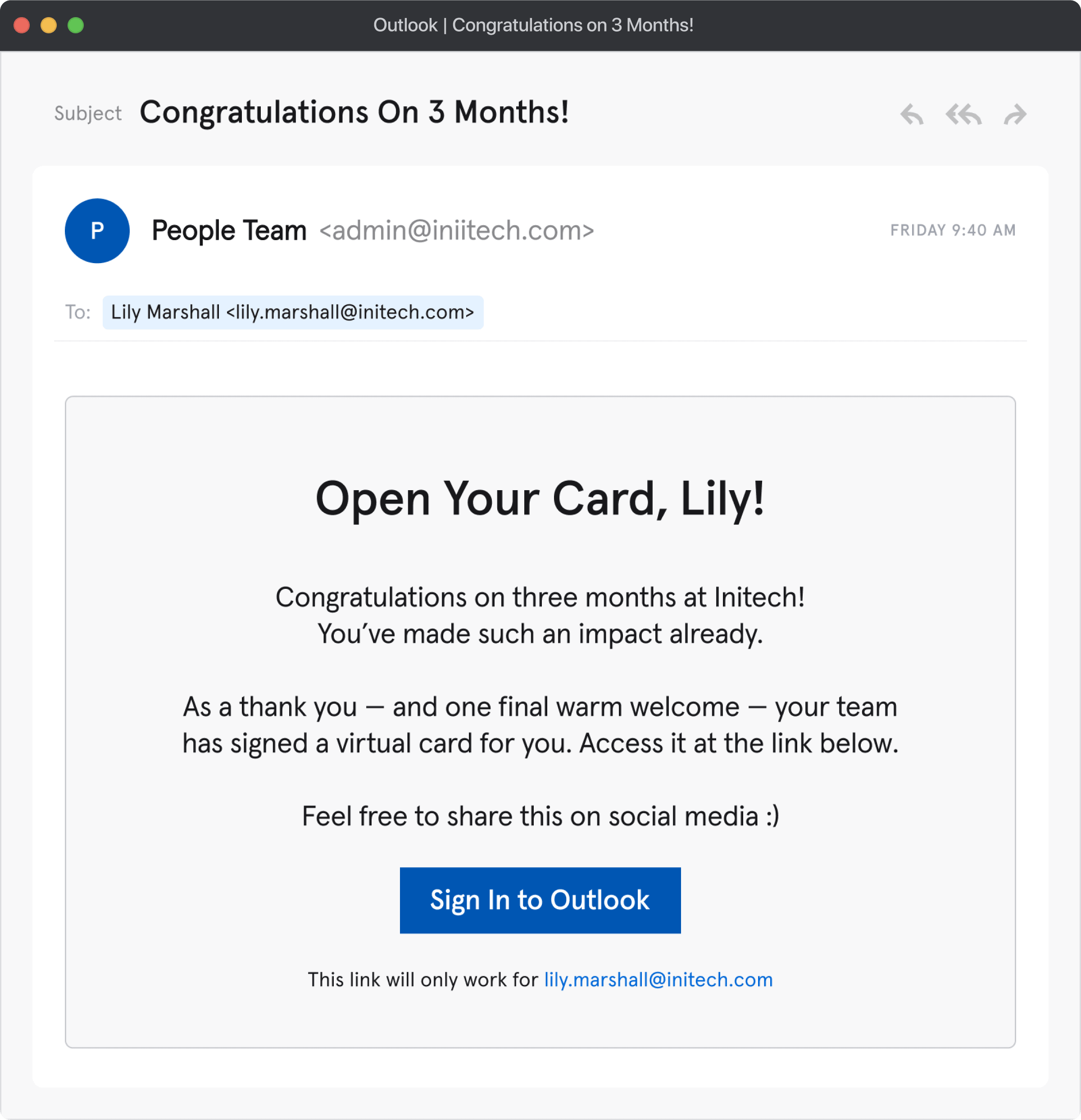
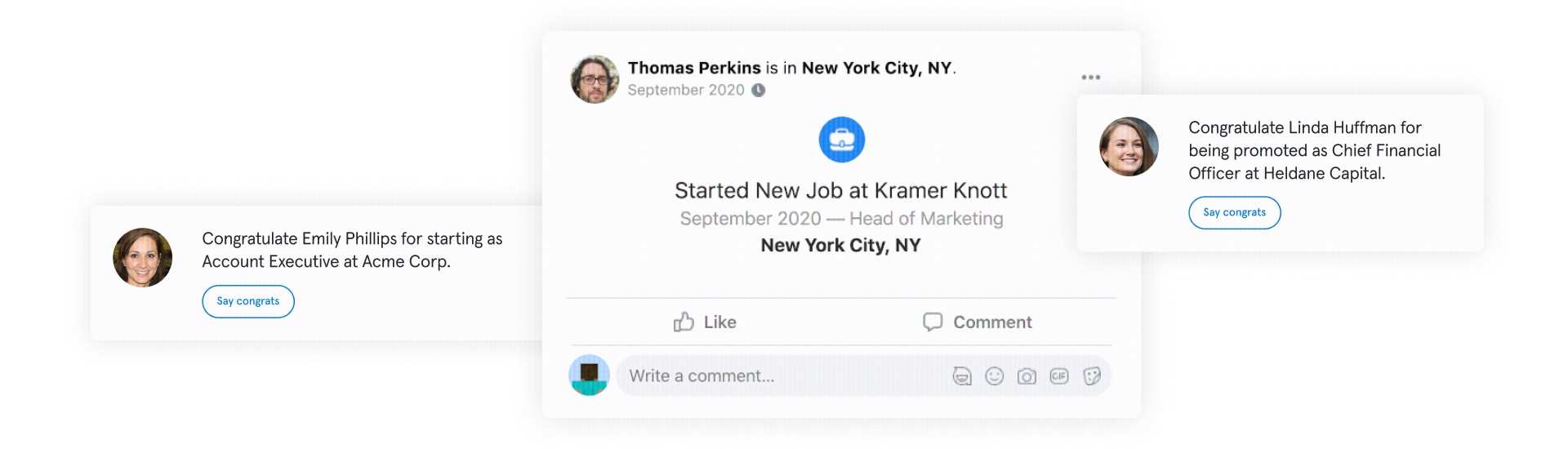
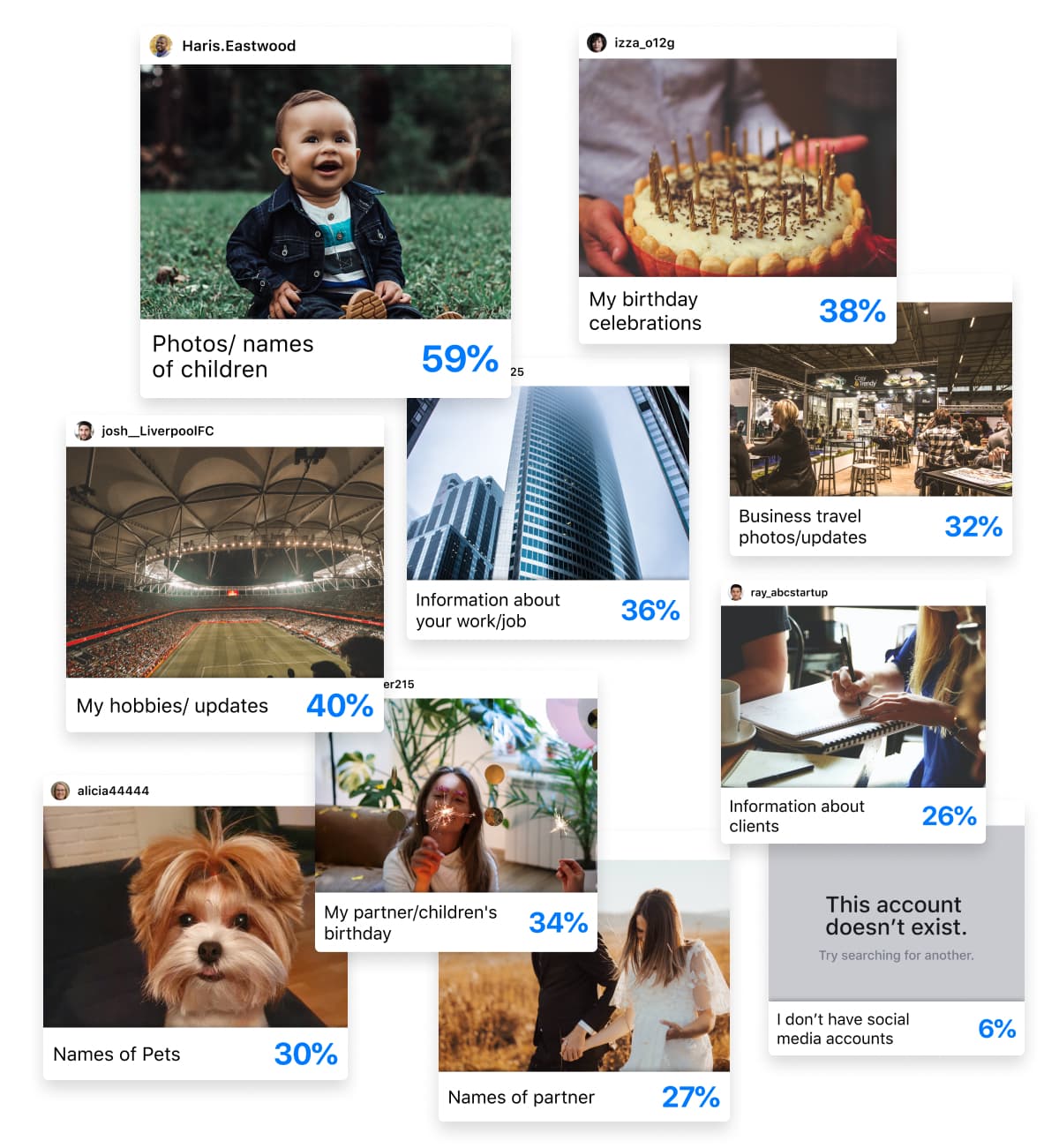
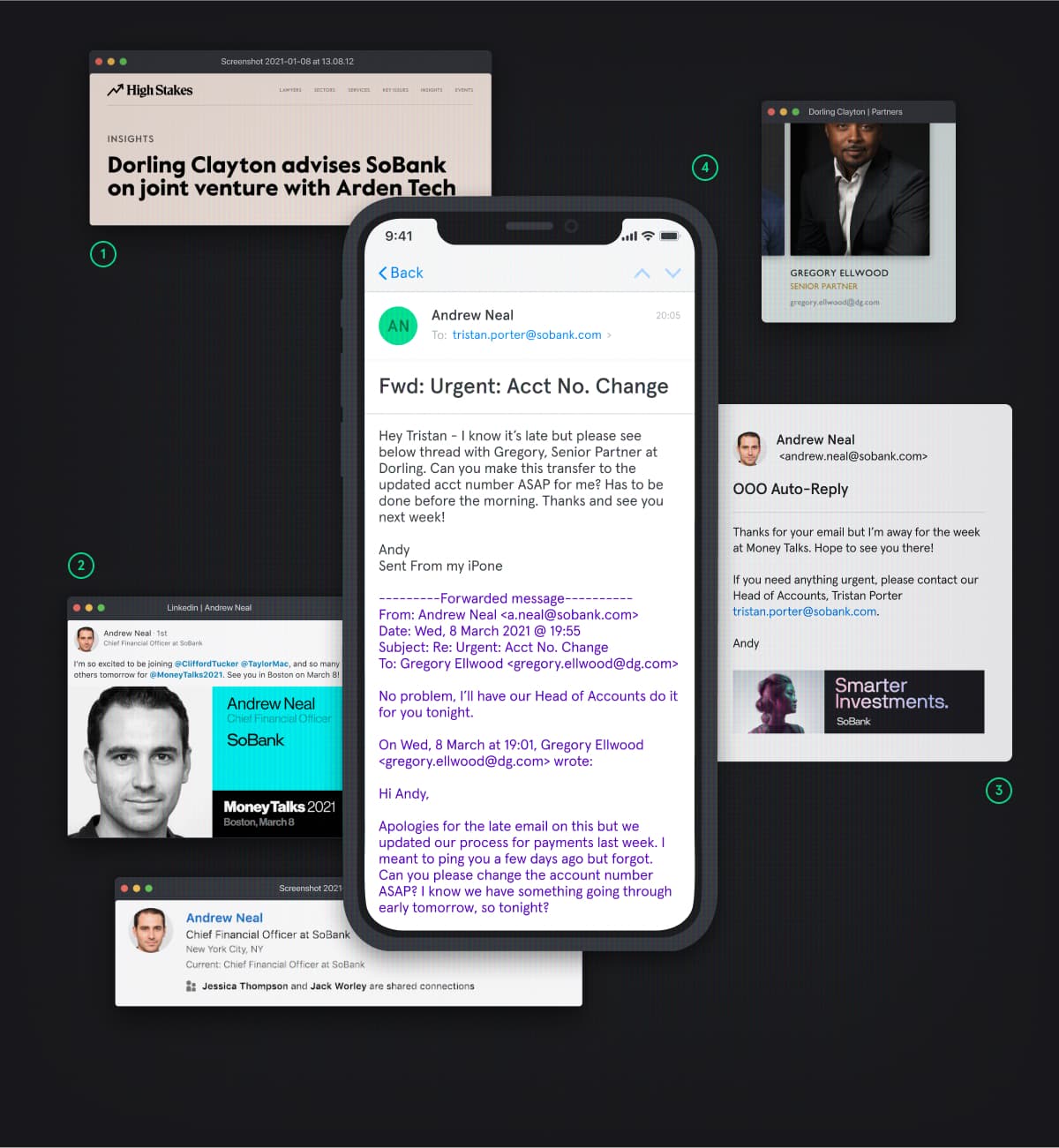
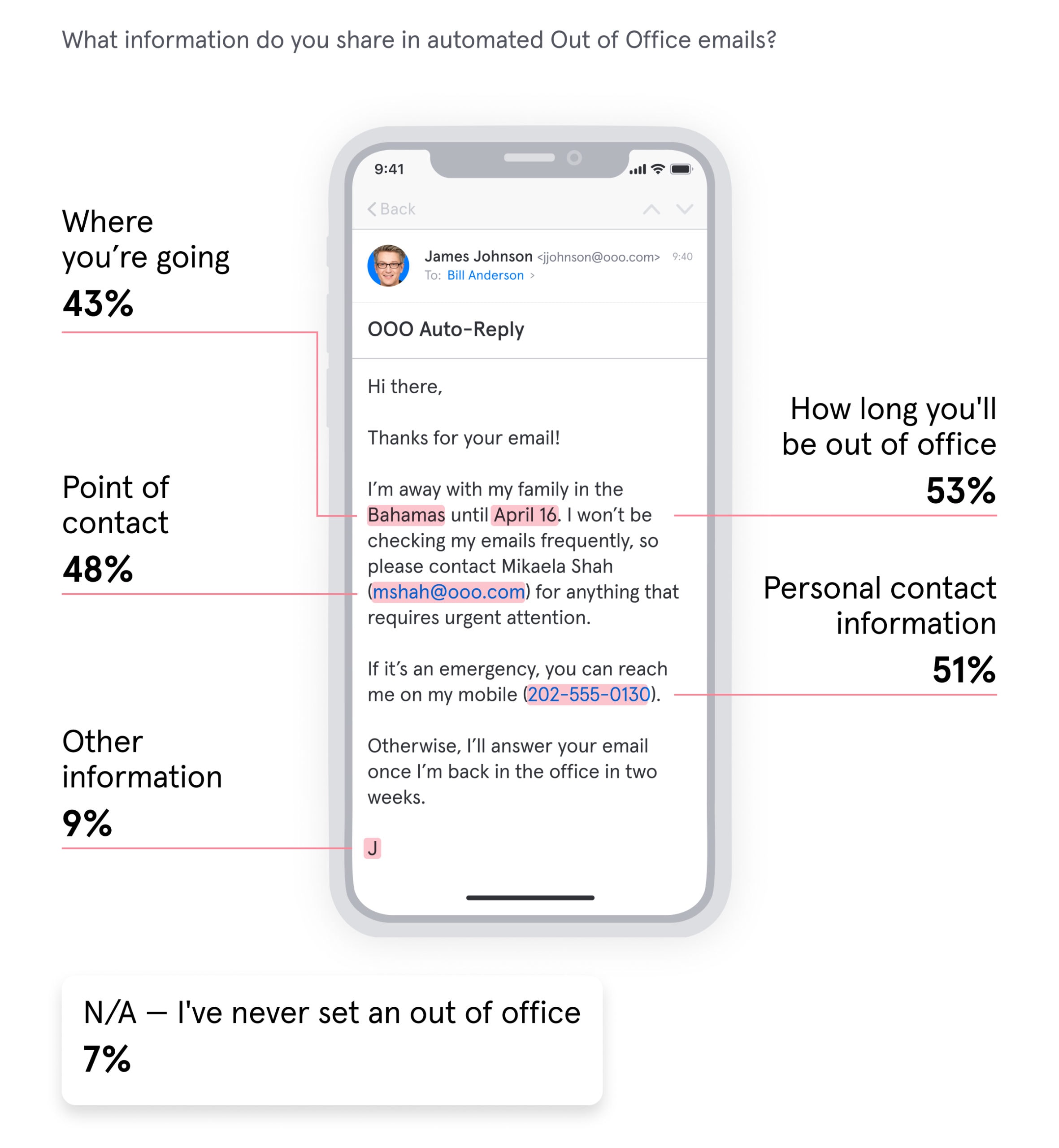
We know what you’re thinking: “So what?”
Every photo we post, status we update, person we tag, and place we check-in to reveals valuable information about our personal and professional lives. With this information, hackers are able to craft more targeted, more believable, and – most importantly – more effective social engineering attacks against people and businesses, leaving PII, trade secrets, and money vulnerable to attack.