Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises.
Unless you’re operating out of somewhere like Somalia, nearly every country in the world has some form of legally binding compliance standards or requirements that cover cybercrime, data security, preventing attacks, litigation, and investigation.
These requirements can further vary (even in the same country) depending on the sector your organization operates in. But whatever the location and sector, to ensure good compliance you need to secure the information your organization handles, and have processes and procedures in place should anything happen to that data.
Security v Compliance
Firstly, let’s explore the difference between security and compliance. Security and compliance are separate functions that help businesses ensure data protection. We take a comprehensive look at the difference between the two in this article, but the following sums it up.
- Security is the infrastructure, tools, and policies you put in place to protect your company’s information and equipment.
- Compliance is the act of meeting a required set of security and regulatory standards. It means protecting the confidentiality, integrity, and availability of data that your company holds.
They’re obviously very closely linked, but each should drive and counterbalance the other.
Six Steps to (Re)designing Your Compliance
Whether you’re new in the role and starting from scratch, or just routinely updating your compliance procedures, there’s a few basics you need to cover. We’ve outlined the six key steps in this handy infographic, but here’s the key things.
Firstly, before you can protect your assets, you have to know what you have. Identify all of your organization’s applications, devices, servers, and people. These items are constantly subject to change, so a regular periodical re-examination is a good idea.
From there, prioritize. Some data is more sensitive than others, some vectors are more vulnerable than others, and you’ll need consent to even process some types of data. More on this below…
After you know what you have – and what’s most important to protect – you can start exploring technology, policies, and procedures that will help you build an effective data loss prevention (DLP) program. This will include network, application, cloud, email, and physical security.
Once you’ve identified what data you need consent to process, the next step is actually formulating the consent request. Where does it appear? How much information do you include? What language do you use? You’ll also need to set-up a process for recording and managing consent and a seamless process for customers to withdraw their consent.
Compliance Requirements Around the World
What sort of compliance rules you have to follow depends on where you’re based and where you process data. For example, the data from any EU citizen is covered by Europe’s GDPR legislation, ‘no matter where in the world the data processing takes place’. Finally, as you’ll see below, different sectors have different types of oversight, too. This is why getting your compliance house in order is crucial to your organization’s smooth governance.
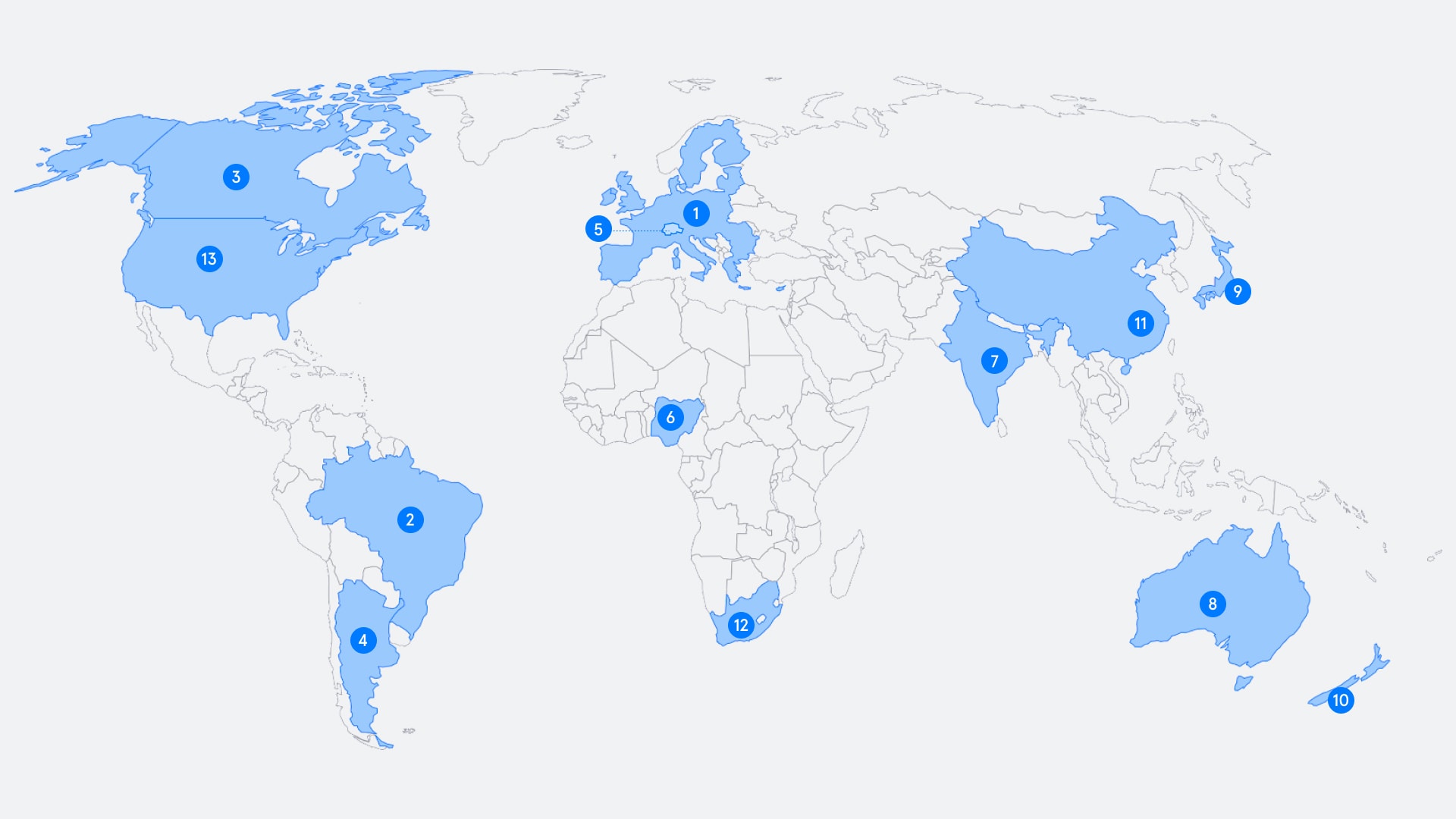
1: Europe — GDPR In 2018 the European Union’s landmark data privacy legislation came into force (there’s a full timeline of its development and impact here if you want to really geek out). GDPR, or adaptations of it, were swiftly adopted by other countries around the world, while others either designed their own set of regulations or beefed up existing ones.
2: Brazil — Brazilian General Data Protection Law (LGPD) Known as “Brazil’s GDPR,” the LGPD imposes data processing principles on all organizations and provides consumers with legal rights.
3: Canada — Personal Information Protection and Electronic Documents Act (PIPEDA). A comprehensive privacy law that applies to all private sector organizations (unless covered by provincial privacy law).
4: Argentina — Personal Data Protection Act. A comprehensive privacy law that applies to all people and organizations doing business in Argentina.
5: Switzerland — Federal Act on Data Protection (FDAP). Like the GDPR, but with smaller fines — and it also applies to “legal persons” (e.g. corporations).
6: Nigeria — Nigerian Data Protection Regulation 2019 (NDPR). A strict data protection law with similar wording to the GDPR, applying to anyone processing personal information in Nigeria.
7: India — Personal Data Protection Bill. A strict and sweeping data protection law working its way through India’s lawmaking bodies.
8: Australia — Privacy Act 1988. Imposes the 13 Australian Privacy Principles, such as transparency and security, on public bodies and businesses with a turnover of over AUD 3 million.
9: Japan — Act on the Protection of Personal Information (APPI). Applies to all private sector organizations and requires consent for the sharing of personal information.
10: New Zealand — Privacy Act 2020. Came into effect on December 1, 2020, with new data breach notification rules, bigger fines, and application to foreign businesses.
11: China — Personal Information Security Specification. One of several laws covering privacy and information security in China — aimed at businesses.
12: South Africa — 2020 saw Protection of Personal Information (POPI) Act finally come into law in South Africa, and it is similar to several other African nation’s data privacy laws. Interestingly, one difference from the EU’s GDPR is that GDPR is extra-territorial, but POPI only applies to South African companies and when data is processed in South Africa. We’ve more on everything you need to know if you’re conducting business in South Africa in our Ultimate Guide below.
13: The USA — Unlike the EU and other nations, the USA doesn’t have a single, overarching piece of legislation. There are some privacy laws at the federal level – most notably Health Insurance Portability and Accountability Act (HIPAA) covering the healthcare sector, California Consumer Privacy Act (CCPA) in California, and the New York SHIELD Act.
The biggest GDPR Fines
Legislators haven’t been afraid to bring non-compliance cases to court. In Europe there have been several high profile fines for major enterprise organizations totaling hundreds of millions of dollars. We list out some of the biggest so far in this article, including such household names as Amazon (€746 million), WhatsApp (€225 million), Google (€50 million) and British Airways (€22 million). Incidentally, if you’re wondering where all that money goes, in the UK at least, it’s passed to the Treasury’s Consolidated Fund, and used to fund all public services, just like tax revenue.
But how has the threat of fines (and subsequent reputation damage) actually affected cybersecurity as an industry? Well, in the few years we’ve had GDPR we’ve seen cybersecurity become a business-critical function, which is big news for an industry that has historically struggled to communicate its value and ROI.
And with that, we’ve seen incredible innovation in security solutions, too. Indeed, the UK’s cybersecurity sector has grown by 44% since GDPR was rolled out. We explore more ways in which GDPR has altered the cybersecurity industry in this piece.
Compliance Legislation is Constantly Evolving
Not only are more countries bringing compliance laws onto the statute books, those that already have them are updating and adapting them too. In the USA CCPA has been updated recently for example. The California Privacy Rights Act (CPRA) – also known as Proposition 24 – passed on November 3, 2020. The CPRA amends the CCPA, pushing the state statute closer to the GDPR.
Consequently, organizations must ensure compliance with the CPPA – integrating the demands of the CPRA – before it takes effect on January 1, 2023. We’ve a full round up of US data privacy laws, and what they mean for your company, here.
As we’ve seen with the CCPA, legislation is under constant review and subject to change. Apply this across several jurisdictions and keeping on top of compliance can be a sisyphean task.
Compliance Guidance by Sector
As stated, compliance isn’t just a geographical issue, it’s also a sector-based one too.
The legal sector, for example, is bound to strict compliance standards as lawyers’ hard drives, email accounts, and smartphones can contain anything from sensitive intellectual property and trade secrets to the Personally Identifiable Information (PII) of clients.
ISO/IEC 27037:2012 for example has guidelines for identification, collection, acquisition,
and preservation of digital evidence.
Healthcare too, is highly regulated with strict regulatory compliance like HIPAA and HiTrust . Healthcare organizations handle massive amounts of sensitive information such as medical records, PHI, and PII, both internally, as well as emails exchanged between third-parties such as hospitals and insurance companies.
Health care spending in the U.S. accounts for 18% of the nation’s gross domestic product, or about $3.5 trillion. That’s like a waterslide on a hot day to criminals which is why health care is plagued by all types of cyber crime. This account of a ransomware attack on a Kentucky optomatrists shows that even the smaller providers are being targeted.
Financial services are also subject to strict data regulation, for example In the USA, the Gramm-Leach-Bliley Act (GLBA) covers any business that is “significantly engaged in providing financial products or services.”
Yet breaches – either intentionally or accidentally – are still happening. In our recent research report, we took a deep dive into Data Loss Prevention in Financial Services and revealed that data loss incidents are happening up to 38x more frequently than IT leaders currently estimate.
Guidance for the energy sector is provided by ISO/IEC TR 27019. Energy companies remain prime targets for attacks because if they don’t pay up, the lights go out. A recent survey found that 77% of U.S. energy companies are vulnerable to ransomware attacks. Even when infrastructure isn’t compromised, there’s still money to be had. One UK energy company even suffered what is thought to be the UK’s first deepfake attack.
Other Data Privacy regulations by Industry
Other sectors and industries are covered by various legislation and information security management guidelines.
App and software developers: Payment Card Industry Mobile Payment Acceptance Security Guidelines. Provides standards for accepting payments over mobile apps.
Children’s online services: Children’s Online Privacy Protection Act (COPPA). US federal law applying to anyone operating a commercial website, online service, or mobile app aimed at children under 13.
Cloud service providers: ISO/IEC 27017:2015. Code of practice providing information security standards from cloud service providers.
Retail/eCommerce/ Payment processing: Payment Card Industry Data Security Standard (PCI DSS). Applies to all organizations that accept, transmit, or store information associated with payment cards.
Manufacturers: Payment Card Industry PIN Transaction Security (PCI PTS). Helps manufacturers create secure payment-processing equipment.
Why Ceos Should Care About Compliance
The impact of compliance has forced cybersecurity from an IT issue to one at C-suite or board level. In fact, by 2024, Gartner believes CEOs will be held personally liable for data breaches. That’s why it’s essential the entire C-Suite understands the importance of privacy, data protection – and therefore cybersecurity – and how these functions can drive meaningful business outcomes.
It’s also worth mentioning that cybersecurity attacks can be highly damaging not only for businesses, but also CEOs themselves, often (very sadly) resulting in their resignation. Examples include Target CEO, Gregg Steinhafel, Equifax’s CEO Richard Smith, LandMark White’s Keith Perrett, and Chris Hylen of Imperva.
It’s not just the CEO, the rest of the C-Suite should also have security top of mind. cybersecurity is a team sport. That means that (like it or not) the responsibility and burden sits with everyone in the company. , particularly the Chief Finance Officer (CFO).
How Tessian Helps
With 85% of data breaches caused by human error, and 90% of phishing occurring via email, it’s clear that securing your human layer is mission critical for your business. Here’s how Tessian does just that.
Prevent Accidental Data Loss: Automatically prevent misdirected emails through in-the-moment and unobtrusive end user alerts; ensure emails are always sent to the right person.
Prevent Insider Threats: Stop sensitive data exfiltration to unauthorized accounts automatically and create custom filters to detect non-compliant email activity.
Protect Against Advanced Phishing Attacks: Protect your business from BEC, spear phishing, payload – less attacks and zero-day exploits; keep your employees, customers, and data safe.
Drive Secure Email Behavior: Tessian’s in-the-moment training contextually guides employees towards safe and compliant email practices, reducing compliance risks.
Gain Visibility and Reporting Capabilities: Gain full visibility on previously unknown threats over email and give administrators the ability to audit, investigate and report data loss events prevented by Tessian.
Never Compromise Productivity: Stay compliant without disrupting work for your employees. Tessian detects anomalous employee behavior with high accuracy, has a very low flag rate, and only surfaces when threats are detected.