Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises.
Today, security leaders aren’t just worried about securing their own networks, email environments, and users. They’re also concerned about how secure the email accounts of their partners, suppliers, vendors, and customers are.
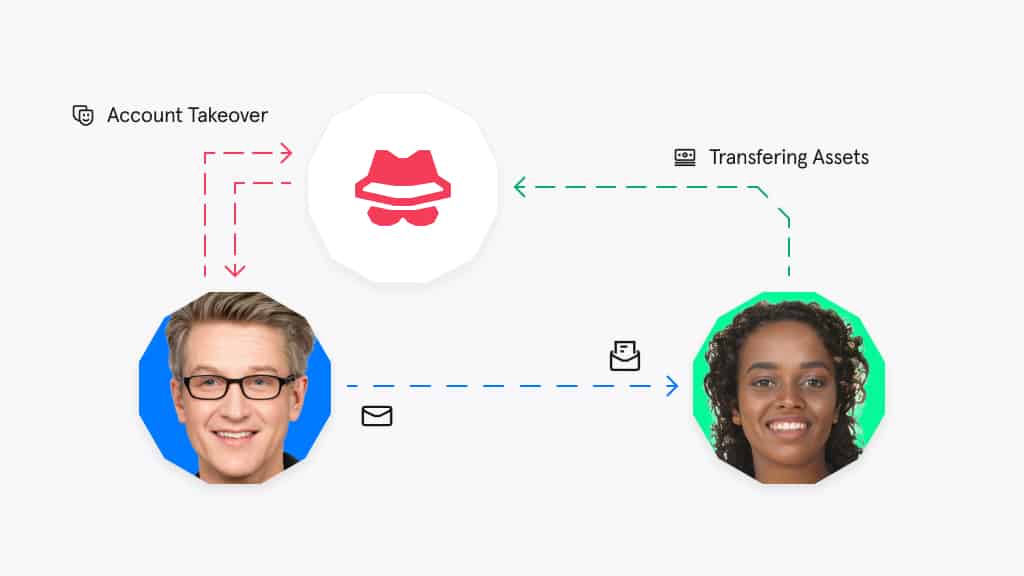
Why? Because more and more often, hackers are compromising impersonating these trusted contacts to gain access to an organization’s systems and data. This is called account takeover.
What is account takeover?
-
What is account takeover?
Account takeover (ATO) is one of the pathways to Business Email Compromise (BEC). But, instead of attacking a target organization directly, the hacker will first gain access to a trusted third-party’s network in order to breach the target.
That means ATO involves two companies.
- A third-party (i.e. vendor, partner, or customer)
- The target company
How does ATO work?
Imagine you work in an accounts department.
You get an email invoice from Syed at ComputerCo, a vendor that supplies your company with computer parts. Syed is polite and friendly (as always!) and tells you that ComputerCo’s account details have changed.
You’re a careful person, so you double-check the invoice with your IT team. They confirm that they made the order. You compare the invoice to ComputerCo’s previous invoices, and it looks identical. The new bank account is located in Boston, where ComputerCo is based.
Due diligence conducted, you go ahead and pay the invoice. You just fell victim to ATO, and unwittingly paid money to cybercriminals. In this case, because the attack was carried out via email, it can also be referred to as Vendor Email Compromise (VEC).
Think you would never fall for a scam like this? Remember, everything looks totally normal:
- The attackers are using the vendor’s regular email address
- The invoice looks authentic
- There’s no perceptible difference in the vendor employee’s email signature or communication style
- Perhaps most importantly — the payment they are requesting is actually due
The only difference is that the vendor’s bank details have changed. So, how do hackers gain access to the networks of trusted third parties? Credential theft, which normally involves one of the following:
- A non-targeted phishing attack
- A targeted spear phishing email
- Brute force attack
- Password compromise
- Leaked credentials
We cover credential phishing in more detail in this article: What is Credential Phishing and How Does it Work?
Why is ATO so effective?
When it comes to solving the problem of ATO, organizations face several challenges.
To start – and as we saw in our example above – they’re incredibly difficult to detect and can evade detection entirely. Why? Because the emails originate from trusted sources and are 100% “real” in terms of sender credentials and metadata.
This means legacy email security tools, which rely on previously known attack signatures to stop threats, cannot detect them. As these emails originate from a legitimate, trusted email account, they will also pass email authentication (DMARC, DKIM and SPF).
The second challenge organizations face is that protecting their own email applications and users just isn’t enough. Security leaders have to address threats from their extended networks too.
The problem is, no organization can control the security of their extended network and they have no visibility of the breaches that happen across their trusted network.
That’s why strong cybersecurity and having the right email security tool can actually be a competitive differentiator, help businesses win more clients and customers, and retain the ones they already have. But, if strong email security helps build trust, a breach will certainly destroy it.
When asked what the number #1 consequence of a data breach is, 21% of IT leaders said lost customer trust.
Examples of ATO
In an interview by NPR, one victim of ATO said he was emailing back-and-forth with a vendor about a $50,000 transfer. What he didn’t know was that the vendor’s email was compromised part-way through the conversation.
Take a look at this excerpt from the interview: “The cadence and the timing and the email was so normal that it wasn’t suspicious at all. It was just like we were continuing to have a conversation, but I just wasn’t having it with the person I thought I was.”
This small business owner only found out that he’d been scammed when the vendor told him he hadn’t received the transfer, by which time the $50,000 was long gone.But the stakes can be much higher than this.
For example, between 2013 and 2015, a team of cybercriminals scammed Facebook and Google out of around $121 million by impersonating a trusted vendor. The scammers in the Facebook and Google attacks used spoof accounts, rather than compromising the vendor’s email account.
Nonetheless, this colossal social engineering attack shows that even the world’s largest companies can fail to spot fraudulent vendor emails. You can read more about email spoofing here.
How to prevent ATO
Although ATO scams can be highly convincing and evade detection from legacy solutions, there are steps your organization can take to protect itself from being targeted by ATO.
Remember that it’s equally important for vendors and other third parties to reduce risks with email security solutions, policies, and procedures.
Email security
Ensuring that you have the right email security tool is a crucial measure all companies should take against ATO and VEC. Tessian Defender, for example, is an email security solution that uses machine learning (ML) to protect accounts against inbound threats.
Here’s how:
- Tessian’s machine learning algorithms analyze your company’s email data, learns every employee’s normal communication patterns. and maps their trusted email relationships — both inside and outside your organization.
- Tessian inspects both the content and metadata of inbound emails for any suspicious or unusual signals pointing to a potential ATO threat. For example, payloads, anomalous geophysical locations, IP addresses, email clients, or sending patterns.
- Once it detects a threat, Tessian alerts employees that an email might be unsafe, explaining the threat in easy-to-understand language.
ATO is rarely perceptible to humans.
Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises, keeping your team, your resources, and your reputation safe.
Payment validation
You should implement internal procedures so employees can validate invoices and payment requests. For example, if a vendor asks you to make a payment to a new account, you may wish to insist upon telephone verification of this request.
Again, these procedures are important, but they aren’t enough on their own. No security policy should rely on human intervention — even the smartest, most diligent employees can be tricked.
If you’re looking for insights into how other security leaders are preventing ATO and other advanced impersonation attacks, check out Tessian’s recent webinar: Spear phishing evolution. How to stay ahead of hackers in 2021.
You can also read our customer’s stories or book a demo to learn more about how Tessian Defender can help protect your organization’s reputation.