Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises.
Let’s start with a definition of email spoofing.
-
What is email spoofing?
Email spoofing involves a person forging an email’s sender address. If you receive a spoofed email, the real sender isn’t the person who appears in the “From” field. Instead, it’s likely a hacker.
While email spoofing can have serious consequences, it’s not particularly difficult for a hacker to do. And, despite the fact that email filters and apps are getting better at detecting spoofed emails, they can still slip through.
Why do people spoof emails?
You might be wondering why someone would want to spoof another person or company’s email address in the first place. It’s simple: they want the recipient to believe that the email came from a trusted person.
Most commonly it is used for activities such as:
- Spear phishing: A type of “social engineering” attack where the attacker impersonates a trusted person and targets a specific individual.
- Business Email Compromise (BEC): A phishing attack involving a spoofed, impersonated, or hacked corporate email address.
- CEO fraud: A BEC attack where the attacker impersonates a high-level company executive and targets an employee.
- Vendor Email Compromise (VEC): A BEC attack where the attack impersonates a vendor or another business in a company’s supply chain.
- Spamming: Sending unsolicited commercial email to large numbers of people.
Now let’s look at the technical process behind email spoofing.
How email spoofing works
First, we need to distinguish between “email spoofing,” and “domain impersonation.” Sometimes these two techniques get conflated.
Here’s the difference:
- In an email spoofing attack, the sender’s email address looks identical to the genuine email address (jeff.bezos@amazon.com).
- In a domain impersonation attack, the fraudster uses an email address that is very similar to another email address (jeff.bezos@amaz0n.co).
When you receive an email, your email client (e.g. Outlook or Gmail) tells you who the email is supposedly from. When you click “reply,” your client automatically fills in the “to” field in your return email. It’s all done automatically and behind the scenes. But, this information is not as reliable as you might think.
An email consists of several parts:
- Envelope: Tells the receiving server who sent the email and who will receive it. When you get an email, you don’t normally see the envelope.
- Header: Contains metadata about the email: including the sender’s name and email address, send date, subject, and “reply-to” address. You can see this part.
- Body: The content of the email itself.
Spoofing is so common because it’s surprisingly easy to forge the “from” elements of an email’s envelope and header, to make it seem like someone else has sent it.
Obviously, we’re not going to provide instructions on how to spoof an email. But we can break down a spoofed email to help you understand how the process works.
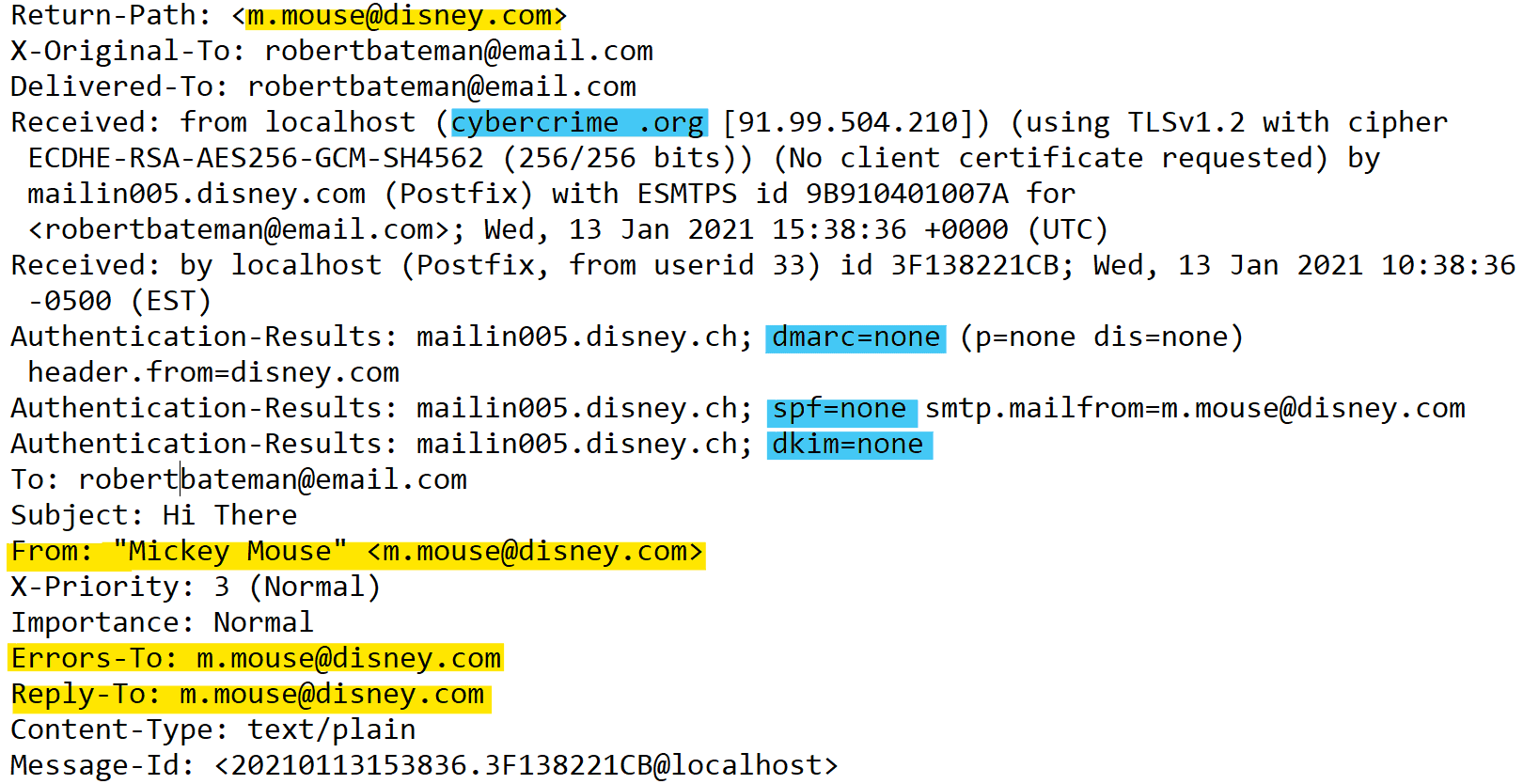
Let’s take a look at the email header:
First, look at the “Received From” header, highlighted in blue, which shows that the email came from the domain “cybercrime.org.”
But now look at the parts highlighted in yellow — the “Return-Path,” “From,” and “Reply-To” headers — which all point to “Mickey Mouse,” or “m.mouse@disney.com”. These headers dictate what the recipient sees in their inbox, and they’ve all been forged.
The standard email protocol (SMTP) has no default way of authenticating an email. There are authentication checks that depend on the domain owner protecting its domain. In this case, the spoof email failed two important authentication processes (also highlighted in blue, above):
- SPF, short for Sender Policy Framework: Checks if the sender’s IP address is associated with the domain specified in the envelope.
- DMARC, short for Domain-based Message Authentication, Reporting, and Conformance: Verifies an email’s header information.
- DKIM, short for DomainKeys Identified Mail: Designed to make sure messages aren’t altered in transit between the sending and recipient servers.
As you can see, DMARC, SPF, and DKIM all = none. That means our spoofed email slipped right through. Here’s how the email looks in the recipient’s inbox:
The email above appears to have been sent by Mickey Mouse, using the email address m.mouse@disney.com. But we know from the header that it actually came from cybercrime.org. This demonstrates the importance of setting up DMARC policies. You can learn more about how to do that here. Note: Disney does have DMARC enabled. This is a hypothetical example! Want to find out which companies don’t have DMARC set-up? Check out this website.
How common is spoofing?
Measuring the precise number of spoofed emails sent and received every day is impossible. But we can look at how many cybercrime incidents involving spoofing get reported each year. A good place to start is the U.S. Federal Bureau of Investigation (FBI)’s Internet Crime Complaint Center (IC3) annual report. In 2020, the IC3 reported that:
- The IC3 received 28,218 complaints about spoofing (up from 25,789 in 2019).
- The losses associated with spoofing complaints totaled over $216.5 million.
Note that the IC3’s definition of “spoofing” includes incidents involving spoofed phone numbers. But we already know that 96% of phishing attacks start with email. There are many examples of harmful email spoofing campaigns, and the COVID-19 pandemic has made it easier than ever for cybercriminals to trick people into falling for these scams.
For example, in October 2021, a threat actor was found to have spoofed email domains belonging to the Philippine government, targeting shipping, manufacturing, and energy companies with fraudulent emails about COVID-19.
And in March 2021, a widespread email spoofing campaign targeting C-suite executives was uncovered. The attackers created spoofed spear phishing emails that evaded “Office 365’s native defenses and other email security defenses.”
Now you understand what email spoofing is, and how serious a threat it can be, it’s time to read our article on how to prevent email spoofing.